In a world like that of the cyber warfare, data is not only being protected; nations are flying at each other, corporations bearing swords with every hack to ensure that hackers won’t be able to compromise their data. Governments treat cyber tactics as a source of espionage, whereas hackers, on the other hand, use exploitation techniques to acquire power and profit. Most importantly, the geopolitical landscape has implications with regards to the cyber policies, as well as surveillance laws, and even interstate conflicts.
Such complex issues have risen from state-sponsored attacks to most controversial surveillance laws. How do intelligence agencies operate in this digital war? More importantly, which threats are real, and how do ordinary citizens and businesses remain safe? This article examines the complex web of Cybersecurity and Geopolitics because understanding it is the first step to staying ahead.
The states and the intelligence agencies
Cybersecurity and Geopolitics is a geopolitical weapon that is embroiled in technology. Governments around the world are investing vast amounts of money to monitor cyber defenses, intelligence operations, and even offensive activities. The intelligence agencies are supposed to formulate policies, monitor threats, and even occasionally conduct covert cyber warfare. With increasing surveillance, heated debates on encryption, and state-sanctioned hacking, these agencies may be seen to be protecting national security, but is that really the case or are they eroding privacy and global trust?
CIA, GCHQ, MSS, and FSB: Cyber Surveillances and Security Policies
The large intelligence agencies constitute the upper echelons of Cybersecurity and Geopolitics efforts, utilizing advanced cyber tools to monitor threats and conduct espionion and to influence various digital landscapes worldwide.
The NSA (National Security Agency – United States)
With its extensive programs for surveillance, the focus of NSA has been on monitoring digital communications, decrypting such communications, and countering cyber threats by adversaries from China and Russia, among others.
CIA (Central Intelligence Agency – United States)
Mostly involved in gathering intelligence by espionage means and covert cyber action, where activities are conducted in settings often characterized as cyber conflicts.
GCHQ (Government Communications Headquarters – United Kingdom)
The main cyber-intelligence agency in UK, securing national infrastructure and monitoring cyber threats from adversaries with whom it collaborates, NSA included.
MSS (Ministry of State Security – China)
China’s intelligence wing carries out cyber-espionage against foreign governments, firms, and critical infrastructures.
FSB (Federal Security Service – Russia)
The most powerful arm of Russia in the arena of cyber strategy, often associated with state-sponsored attacks against other countries, interference in the electoral process, and digital propaganda campaigns.
While they might allege to be protecting national security, the ethical and legal implications of their growing power on surveillance can be felt globally.
U.S. and U.K. Cybersecurity Policy and Controversy
However, the amount in which these governments have indulged themselves relative to intrusions upon individual reserved freedoms is always embroiled within a massive argument for national security.
Mass Surveillance Program:
The leaked file between Edward Snowden and the NSA and GCHQ, including thousands of pages of how these agencies gather huge data from the civilians and foreign governments.
Encryption Backdoor:
The UK government is politically lobbying on technology giants like Apple, forcing them to degrade their encryption systems for intelligence agencies to gain access to the user’s private data. The critics, however, declare that this is a global security threat.
Legislation and Treaties
The continued attempts to effect international treaties on Cybersecurity and Geopolitics by the U.S. and the U.K. have been thwarted by critics who argue that such treaties prioritize surveillance over individual privacy. The proposed Global Surveillance Treaty is one such example creating resistance among human rights groups and technological companies.
As the government extended, the balance between security and privacy began to shift significantly under threat.
Effects of government regulations on encryption and privacy
Encryption has become one of the most intensely debated technologies in Cybersecurity and Geopolitics today. It is that technology which conceals any private communication via e-mail (and all other forms of electronic communication) from prying third-party eyes. Governments argue that such strong encryption helps terrorists and criminals conduct their activities in a covert way, while advocates for personal privacy warn that such weaknesses should not be allowed to open the doors to hackers and authoritarian overreach.
Apple Vs governments
The UK and other international governments demand backdoor into encrypted data; subjecting the tech companies either to comply or go legal action. Apple is resisting this with the claim that it will jeopardize user security across the globe.
The ‘Going Dark’ Dilemma
Intelligence agencies claim that it is now extremely difficult to track criminals using encryption technology. However, security experts argue that if this comes to pass, it would lead to billions of users being exposed to cyber levels of threats.
China and Russia’s Tough Cyber Laws:
Companies are required to store the data of users on their territory and give access to government officials if they need this information. These regulations raise serious concerns as to how much state control exists over the digital content.
This war is barely beginning. Advances in technology will continue to change how governments and the criminals misuse the self-same technology.
Cyber security threats are from nation-states and hackers
With the growing global integration, threats to cyber security have transformed from the aforementioned individual hackers to include state-sponsored, cyber-espionage, and digital war-based threats. Such threats are generally more sophisticated and dangerous than ever before, as nation-states adopt the cyber tool for advancing their political, economic, and military agendas. Alongside this are, among others, hackers ranging from lone actors to organized syndicates of cybercriminals. Understanding the scope and characteristics of this threat is crucial for businesses, governments, and individuals.
Cyber attacks in conflict or hostile states and organized cyber gangs
Cyber-attacks from hostile nations are increasingly becoming common and more complex. Nation-state views involve cyber capabilities in its defense and offense strategy by infiltrating other countries’ infrastructures, stealing sensitive data, and disrupting systems: Most of these cyber-attacks have a political motive to destabilize or influence the target country.
Cyber Operations of Russia
Russia has been associated with several international and high-profile cyber-attacks, such as meddling in the 2016 U.S. presidential elections, the NotPetya ransomware attack in 2017, and continuous operant activities against critical infrastructures worldwide. The Russian government is said to use its cyber operations for political leverage, through economic espionage, as also as military strategy.
Cyber Espionage of China
China has been accused of indulging into vast cyber-espionage ventures in the act of stealing intellectual property, trade secrets, and government data. Chinese hackers have penetrated from major corporations to national security agencies. Notably, though, the Chinese government denies the allegations. However, the scale as well as the sophistication of attacks suggest state backing.
Iranian and North Korean cyber techniques
Like North Korea and Iran, the two counties are making use of cyber capability to push their geopolitical end. Iran has a historical tendency to strike at the critical infrastructure of the U.S. and Saudi Arabia while North Korea is better known for its unrelenting hacking campaigns targeting financial institutions, cryptocurrency exchanges, and nuclear research organizations.
Thus, these gangs are working all over the world, usually with some level of state sponsorship or at least tacit approval. These are operations of ransomware, data breaches, and financial fraud, essentially with a focus on both public and private sectors.
Case Studies: U.S. Treasury Hack, UK Security Vulnerabilities
Cyber-attacks have implications, not only against military and intelligence services, but also against chief Government institutions and critical infrastructure. A very publicized attack in 2020 on SolarWinds may be perhaps the biggest breach that threatened the U.S. Treasury and numerous other government agencies. Hackers from Russia allegedly state-sponsored intervened through software updates of SolarWinds to get access to sensitive networks and steal confidential information
Another interesting case is the relentless threats against U.K. critical infrastructures-the targets of both foreign enemies and criminal groups. The U.K. government has been stepping up its initiatives, through agencies such as GCHQ, against cyber-attacks, although vulnerabilities exist. Reports are speaking of major risks to the U.K. from Russian cyber attacks levelled against targets ranging from energy grids to healthcare systems.
These attacks represent much more than impacts to the technical defense; they represent actual cracks into the political tensions between nations. Cyber-attacks emerging as an accepted tool for Statecraft now serve as the constant reminder of how espionage and sabotage can be executed without firing a single bullet.
Role of Intelligence in Stopping Cyber Warfare:
Except for intelligence agencies around the world, the latter have really ramped efforts on prevention of cyber warfare. The agencies monitor the digital communication that is being tracked by cyber threats or in most cases refer to offensive computer operations to disrupt or disable enemy infrastructure. However, the glare of values is often blurred between defensive and offensive operations.
Espionage – Cyber:
Intelligence agencies exploit cyberspace for intelligence. They hack into foreign governments, corporations, and research institutions to steal confidential information through various cyber tools. Most operations are covertly designed, and discovery leads to international tensions.
Offensive Cyber Capability:
A U.S., Russia, or China can achieve impressive capabilities to strike an enemy at all levels: military, energy, and communication. Such strikes can dislocate an enemy’s economy and have grievous effects at the political level, anywhere, without a single troop marching into battle.
Global cooperation and defense in cyberspace
Countries may go to war with each other in cyberspace, but such a war does not rule out the growing cooperation. Countries have started working together to exchange threat intelligence, harmonize Cybersecurity and Geopolitics standards, and create defenses against common threats. The Budapest Convention is one of the many international treaties that make it mandatory to facilitate global cooperation against cybercrime but not without some disagreements surrounding privacy and data protection.
Private Cybersecurity and Geopolitics and Geopolitics companies, apart from intelligence agencies, also help immensely in chasing after these cyber threats and managing them. FireEye, CrowdStrike, and Palo Alto Networks are examples of companies that assist in containing and countering sophisticated cyber attacks.
Global Surveillance and Privacy Issues
As the digital world expands, governments are turning toward surveillance for national security and counter-cyber threat objectives. Nevertheless, pervasive surveillance triggered considerable debate over the infringement of privacy rights and possible authoritarian tools. The flip side of this scenario exhibits greater dilemmas between national security interests and individual freedoms while policymakers push for global surveillance regimes and privacy-invading technologies. This section looks into the global dynamics of surveillance, the controversial methods adopted by governments, and the ongoing fight for privacy protection.
The Proposed Global Surveillance Treaty and Its Implications
The push toward a Global Surveillance Treaty is one of the most contentious matters in Cybersecurity and Geopolitics and privacy today. With the support of certain world powers, the treaty seeks to create an international framework to combat cybercrime, track terrorists, and enhance intelligence-sharing among nations. The rationale is that governments should be able to gain access to data across borders with minimal restriction. Very soon, alarm bells were ringing for privacy advocates, human rights organizations, and tech corporations.
Why Governments Support the Treaty
Governments feel there is need for a global treaty to tackle cross-border cybercrime and terrorism since the very perpetrators are protected by the borders of different States such that apprehending and convicting them becomes difficult. They argue that standardized surveillance procedures and access to data will empower Countries to properly conduct surveillance over and discontinue malicious activities such as hacking, trafficking, and terrorism.
Opposition to the Treaty
Critics of the treaty claim that it would facilitate mass surveillance, which is likely to be turned against political dissidents, journalists, and activists by authoritarian regimes. Countries such as Russia or China with low levels of respect for human rights would use these kinds of treaties for the sake of surveillance and to gag dissent.
Repercussions for Global Tech Companies
Next, if passed, local laws would take precedence over global tech companies like Google, Facebook, and Apple, thereby granting governments access to user data like never before. The privacy advocates warn that this compromise could weaken the whole protective architecture preventing hijacking of personal data.
The proposed global surveillance framework is still a point of contention, and its future will depend upon the extent to which governments and civil society can reconcile security needs with the right to privacy.
The Battle Over Encryption: Apple vs Government Decryption Demands
Critical to the debate on global surveillance is encryption, which secures communications and protects user data from unauthorized access. Encryption protects everything from Internet banking to private conversations, while governments have increasingly sought to undermine encryption for so-called national security purposes.
Demands for Backdoor Access
The British government has demanded that tech companies, including Apple and Google, give them “backdoors” into encrypted devices and messages. So that law enforcement could circumvent encrypted channels in their investigations, especially ones relating to terrorism and criminally-motivated activities. The tech companies such as Apple have countered these demands fiercely, stating that backdoors would ultimately weaken security and privacy for all users, not just criminals.
The ‘Going Dark’ Problem
Law enforcement claims that strong encryption gives criminals the environment in which they can work in the digital shadows, creating difficulties in basically every area of investigation-from terrorist activities to the exploitation of children. Conversely, privacy advocates argue that compromising encryption will place people at greater risk for extra attacks, with hackers being able to exploit backdoors or other vulnerabilities in security implementation.
The Global Divide
Different countries tend to have different approaches toward encryption. The U.S. and other Western nations have generally favored the application of strong encryption for protecting personal liberties, while countries like China and Russia pushed for policies that would give more state access to encrypted information. The divergence in these approaches has caused a fragmented global legislative landscape on encryption.
Amaze, one is very intelligent:
On-going debates about encryption continue to stand in the way of appreciating how delicate the balance that should be struck between considerations of national security and individual mosaic security ought to be. And the more technology advances, the more complicated this issue becomes.
Mass Surveillance Ethics and Future:
As series of questions posed an ethical character to the development of technologies for mass surveillance, conscripts in the changed digital milieu power to limit state intervention in private matters. State after state, tend to argue the need for surfacing about terrorism, cybercrime, or espionage, but there still remains the possibility that they will intrude into the individual collective or democratic rights through unchecked proliferation in the number and types of such tools.
Ethics of Surveillance:
Though these mass surveillance systems may provide a justification for national security, the misuse of such systems can result in violation of rights that include the freedom of expression, the freedom of association, and the right to privacy due to the volume of data collected by them from an ordinary citizen regarding his/her online behavior, location, and personal communications.
Face Recognition and AI
Public spaces are monitored with technologies such as facial recognition and with AI because their sightings also come online to track an individual’s movements quite often. These technologies could be great for tracking down criminals or stopping terrorist attacks; however, some criticism is levelled at the technologies, alleging that they could become misused and directed toward groups such as racial minorities or political dissidents.
Increasing Power of Corporations
Not all monitoring activity comes from government sources; some comes from other private entities. Take large tech companies, for example: Google, Amazon, Facebook; these are data-hogging machines that can sell personal data for targeted marketing purposes, worth millions and billions of dollars. Of course, their argument uses their data for improved services, but there are weighty concerns or strings attached with this increasing concentration in fewer hands.
Privacy by Design
The more privacy protection becomes popular, many organizations start adopting the privacy by design approach in which privacy is embedded into the products and services from when they are built and to restrict future plans for when a stakeholder must use the service.
The future of mass surveillance will, therefore, in all probability, be a combination of stringent enforcement and enhanced privacy protections. The real test, however, lies in striking the balance that permits states to safeguard national security without impinging on citizen rights.
Security and Geopolitical Intelligence Careers
Cybersecurity and geopolitical intelligence are becoming more connected to each other, creating amazing demand for professionals with training and skills in both fields. Increasing incidences of cyber warfare, espionage, attacks from state-sponsored programs have caused a sudden boom in the job market, with intertwined disciplines, requiring high technical skills in Cybersecurity and Geopolitics and the very much wider political landscape of things. If you’re just entering the job force or looking to change gears, being knowledgeable about skills and pathways available can unlock many fantastic positions that an individual can find in the field.
How to Start On Cyber Security or Intelligence Analysis During the Career
The massive cybersecurity and geopolitical intelligence fields have several job opportunities for everyone, primarily into main categories of entry according to one’s set of eyes or lenses. For the most, including the formal learning, special training, and practical experience, these are life elements that be included on the pathway entry to the actual field.
Education and Certifications
The foundation of any cybersecurity/intelligence career is education. Degrees in disciplines such as computer science, information security, political science, international relations, or other fields related to the profession empower individuals with essential knowledge for the job. Apart from these degrees, industry credentials like CompTIA Security+, Certified Information Systems Security Professional (CISSP), and Certified Ethical Hacker (CEH) will provide an add-on to the skills and show current expertise in the field.
Those looking for intelligence analysis-related careers would find their take-off degrees such as political science, international relations, or criminal justice beneficial; specialized programs on cyber intelligence, geopolitics, or risk analysis would advance such job candidates in the market.
Internships and Entry-Level Positions
One of the best ways to break into the industry is by getting hands-on experience through internships or entry-level positions. Several government agencies, intelligence consultancies, and private Cybersecurity and Geopolitics firms have available internships, which gain real learning experiences with the field. Internships allow you to develop practical skills, connect with professionals, and understand what is required of cybersecurity and intelligence jobs.
Soft Skills for Intelligence Roles
In addition to hard skills, the field of intelligence analysis is also the practical training provided in critical thinking and problem-solving abilities, as well as the ability to analyze complex geopolitical situations. Further communication skills are required for writing reports and dumping into findings those data collections. Understanding the dynamics in world politics, economics, and international law will make sense of the data you collect.
Best Courses and Certifications for Cybersecurity Careers
As existing areas are challenged in their rudiments and complexities to exist or survive and continue to evolve, continuous guidance, learning, and edification become imperative. With technical courses and specialized certifications, one can become proficient, recognized, and updated with an array of threats from these specializations to refining career skills.
Technical Cybersecurity Certifications
Examples of top certifications in the cyber field include:
- Certified Information Systems Security Professional (CISSP): This certification is generally accepted and sought after and covers quite all aspects of Cybersecurity and Geopolitics, in particular, risk management, security architecture, as well as other topics, including cryptography.
- Certified Ethical Hacker (CEH): This certification is for individuals who require becoming penetration testers to identify vulnerabilities within networks and systems.
- Certified Information Security Manager (CISM): This sort of certification covers information security management, best suited for those aspiring towards leadership positions within Cybersecurity and Geopolitics.
Cyber Intelligence Programs
For those inclined towards understanding how Cybersecurity and Geopolitics converges with geopolitics, particular programs have in-depth insights into the intelligence community’s role in actually managing the cyber threats:
Master of Science in Cyber Intelligence
A master’s degree that takes integrated Cybersecurity and Geopolitics with intelligence analysis and prepares students for confronting cyber threats in the scope of geopolitics.
Geopolitical Risk Analysis
Courses on global politics and economic security provide an overall context for understanding intelligence professionals’ analytical scope for Cybersecurity and Geopolitics threats.
Cybersecurity Bootcamps and Online Courses
Most aspiring Cybersecurity and Geopolitics professionals would simply go to boot camps or online programs in order to take these courses within a very short time frame. From sites like Coursera, edX, and Udemy, courses on ethical hacking, network security, cryptography, and others are available, supplemented by hands-on labs cases from the real world.
Skills Necessary for Geopolitical Risk and Intelligence Analysts
Persons engaged in and trained for work in geopolitical risk analysis and intelligence analysis shall have a common mark that combines knowledge from both cyber and signification studies. The analyst plays a key-niche role between difficulties caused by cyber threats and political actions at the global level to identify as well as mitigate risks due to hostile states, cybercriminal actions, or even global economic shifts resulting therein.
Technical Skills
Knowledge of certain cyber security aspects such as network security, malware analysis, encryption, and vulnerability management is imperative. Domain experts also advise those venturing into cyber intelligence to be proficient in tools like Wireshark, Kali Linux, and Metasploit. Generally, and not limited to the above, being knowledgeable in analyzing data from different sources, including open-source intelligence (OSINT), can provide insights into potential threats.
Political and Analytical Skills
Political education is necessary as regards international relations and global trade, defense conditions, and economic strategizes. The analysts should be capable of critiquing how the political events influence Cybersecurity and Geopolitics like increasing cyber-attacks after foreign policy change. Analysts should also possess the capacity of data trend spotting, impact assessment of cyber incidents, and ability to generate actionable proposals for decision-makers.
Communication and Reporting
Finally, the intelligence analysts should present a lot of complicated information clear and concise. Whether this is in written form through reports or orally in presentations, effective communication is vital for making sure the analysis can simply be understood and thus acted on. Briefing of decision-makers about the potential effects of cyber threats in the geopolitical context should also be conducted by analysts.
From Cybersecurity to Intelligence Specialization Careers
The world of cybersecurity is an expanding discipline, which opens various avenues for specialization-from penetration testing to cyber threat intelligence, with much more in between.
Penetration Tester (Ethical Hacker)
Ethical hackers use techniques and tools of hacking to identify weakness in systems and networks before the exploitation by malicious individuals. This job needs a very high level of technical skills coupled with knowledge of hacktools and ability to think as an attacker.
Cyber Threat Intelligence Analyst
An analyst, who understands how currently reckless cyber hazards can forecast an incoming onset of breaches through monitoring activities on the dark web, stitching and tracing hackers’ group tactics, and providing strategic advice on risk mitigation.
Geopolitical Risk Analyst
The focus is on how political and economic, or military, events influence the cybersecurity landscape. Thus, geopolitical risk analysts are attached to government agencies, MNCs, and security firms, giving insight into the prospective risks posed by foreign governments or terrorist organizations.
Cybersecurity Consultant
In an organization, such consultancies help assess and improve the level of cybersecurity. They have expert advice on how to implement security measures, respond to incidents, and prepare for the onslaught of future threats. This role requires a strong dose of both technical and advisory skills.
Important Resources along with Learning Materials
Being conversant with the latest changes and trends in Cybersecurity and Geopolitics, espionage, and geopolitics is critical for professionals in these fields. As technology and threats advance faster and faster, continuous learning is required to keep users in touch with developments and stay ahead of new dangers. In this part, we would review some of the best espionage and cybersecurity history books, recommend university courses and professors, facts and many other useful resources for cyber-security professionals.
Best Books on Espionage and Cybersecurity History
General books could take a reader through some aspects of the history of espionage and cybersecurity to provide background for understanding contemporary threats and strategies. Whatever the specific interest-from the development of espionage to the history of cybersecurity or the intersection of both worlds-there are many books will be available.
Best Espionage Books
“A Cold War classic”, John le Carré wrote, “that describes all the twists and grittiness of the late Cold War with its moral dilemmas and ethical gray areas of intelligence and its implications”.
History of the CIA in a very brutal way”. As this book goes on to highlight intelligent observations on the agency’s work-from successes to failures-over several decades since its very beginning.
The Secret History of MI6
The History of the British Intelligence Service”, Keith Jeffery: This careful account of MI6-the secret intelligence service of Great Britain-hardly skims the surface of its history, major operations, and characters behind the agency.
Some Great Books on Cyber Security History
Cliff Stoll’s Cuckoo’s Egg
A gripping account of one of the very first major cases of cyber espionage, it follows Stoll, a systems administrator, in his investigation of a hacker ring stealing U.S. military secrets.
Cybersecurity and Cyberwar
What Everyone Needs to Know by P.W. Singer and Allan Friedman: This book provides a very approachable history and present view of Cybersecurity and Geopolitics with its intersections among national security; it contains a very detailed and lucid description of cyber threats and policies.
Simon Singh’s The Code Book
The Science of Secrecy from Ancient Egypt to Quantum Cryptography: This book is a thorough history of the making of codes, reaching to its modern significance in the realm of Cybersecurity and Geopolitics–a worthy reading for anybody seriously interested in the technical side of security.
University Courses and Professors Worthy of Recommendation
That is the best sort of groundwork that can be laid for specialization in Cybersecurity and Geopolitics, espionage, and political intelligence. It does not matter whether the student wants to earn a degree or just take a few online courses; the following are some of the most recommended for taking courses from these institutions and professors.
Premier University Programs for Cyber Security
Stanford University – “Computer and Network Security”
It is one of the better-known courses in Cybersecurity and Geopolitics covering secure programming, network security, and cryptography. Stanford’s reputation and lineage in cybersecurity would highly vouch for this course.
Massachusetts Institute of Technology – “Advanced Cybersecurity”
At MIT, studies in the field of Cybersecurity and Geopolitics embrace subjects like data privacy, security protocols, and current advanced defense strategies against cyberattacks in very much detail. The courses offered by MIT have a great reputation for their intensity and relevance.
University of California, Berkeley – “Introduction to Cyber Security”
UC Berkeley offers this introductory course wherein fundamentals of Cybersecurity and Geopolitics are drifted in a beginner-friendly fashion, including ethical hacking, threat analysis, risk management, and cryptography.
Recommended Professors
Bruce Schneier is a scholar at Harvard University; He is considered one of the top experts in Cybersecurity and Geopolitics. His writings on cryptography as well as cybersecurity policy have been profoundly influential.His teaching and writing present a foundation for the study of security systems and risk management.
Dr. Dorothy Denning (Georgetown University)
A forebearer in the field of cyber security, Dr. Denning’s studies are among network security, cryptography, and cyber security policy. According to the academic world, she is a highly respected name for her work in understanding the technical aspects of cyber security as very much an intersection of law and technology.
Dr. Matt Blaze (University of Pennsylvania)
Another key figure in cyber security research, Dr. Blaze’s work has included studies of issues and technologies related to cryptography, privacy, and computer security. Much of his work examines the social and political consequences of these technologies.
Quick Facts and Resources for the Cybersecurity Professionals
Cybersecurity professionals are quick and accurate tons of information to outsmart cyber threats. Here are some of the highlighted resources that make good quick facts for anyone in the field.
Top Cybersecurity Websites and Tools
Cybersecurity & Infrastructure Security Agency (CISA)
U.S. government agency wealth of resources gleaned with regard to national Cybersecurity and Geopolitics defense-from threat intelligence to guidance to the incident response. CISA materials are priceless for professionals of both government and the private sector.
SANS Institute:
The SANS Institute is a leading Cybersecurity and Geopolitics training organization offering resources, training, and certifications for professionals at all levels. Industry forums recognize their courses among the finest for building practical skills in Cybersecurity and Geopolitics.
Krebs on Security
This is an investigative reporter by the name of Brian Krebs This Cybersecurity and Geopolitics blog provides detailed articles on latest security threats, breaches, and vulnerabilities. Professionals wanting to remain in the know of incoming threats should definitely read this blog.
Quick Cybersecurity Facts
Cyber Crime on Course to Reach an Annual Cost of $10.5 Trillion by 2025: High among the global concerns in costs of countries over the coming decades is cybercrime, which, as Cybersecurity and Geopolitics Ventures reports, would be exceeding $10 trillion annually by 2025.
The Rise of Ransomware Attacks
Spurt in Today’s Ransomware Incidents is another critical world trend in Cybersecurity and Geopolitics. Hostaged businesses worldwide have, therefore, caused great disruption and considerable wealth loss.
More than 50 percent of All Data Losses Acquired from Hacking
The 2021 edition of the Verizon Data Breach Investigations Report tells us that hacking has more than half of all breaches reported in 2021, involving phishing and exploiting vulnerabilities.
Cybersecurity Career Resources
- ISC2 Cybersecurity Certification: ISC2 has globally-renowned certifications such as CISSP (Certified Information Systems Security Professional) and CCSP (Certified Cloud Security Professional), which hold very high value for careers in Cybersecurity and Geopolitics.
- CyberSeek provides a comprehensive map of Cybersecurity and Geopolitics job opportunities across the United States, career pathways, certifications, and resources that in cyberspace from an entry-level to an advanced position.
Cybersecurity comes into a changed world
When we look into the future of Cybersecurity and Geopolitics, we must consider the larger context it is evolving. The future landscape itself is casting shadows from geopolitical changes, and revolutionizing technologies accompanied by a growing number of global challenges. This short section introduces some of the important things: what it may mean for the collapse of the world powers; the way unified intelligence and defense systems will become; how individuals and businesses could prepare themselves against emerging threats.
The Collapse of Global Powers and Its Impact on Cybersecurity
These shifts in power across the world will have huge ramifications for Cybersecurity and Geopolitics. Where powers are now finding challenges within and outside their territories, new geopolitical actors come up, the global Cybersecurity and Geopolitics environment is rendering itself much more fragmented and unpredictable.
Geopolitical Instability and Cyber Threats
In a world, where the geopolitically balancer always remits to injury, indeed the proclivity to cyber threats because of political conflicts would increase. How states would be able to deal with such absolution would case if countries feel abandoned and exposed to potential harms, wherein cyberassaults are one option an asymmetric warfare method does on critical infrastructures or steals classified information for a nation’s advantage for its political or economic dividends.
The Collapse of Old Powers
Potentially, given possible changes to the U.S. and other singular major global players as strengthening, it creates power vacuums, resulting in opportunities for small or more unstable countries to accrue power. They simply don’t have the technological framework or support to maintain good Cybersecurity and Geopolitics, so they become prime targets of these more powerful states or even cybercriminal groups.
Furthermore, with the decline of established power stables, international cooperation for collective Cybersecurity and Geopolitics tends to diminish, along with the possibility of fighting transnational cybercrime or dealing with threats across borders or coordinating defensive measures.
Cybersecurity as an Instrument of Political Influence
Emergent powers might also find ways of asserting themselves with respect to the traditional great powers through cyber measures as these latter powers continue to lose ground. Normalizing cyber attacks as a primary technique of influence, detraction of opponents, or restructuring global policy will begin. Countries like Russia or China, with mature cyber capabilities, are pioneers in this now standard in the use of cyber means for political manipulation, espionage, or influence campaigns.
The Future of Unified Global Intelligence and Defense Systems
One of the areas that must be addressed with regard to the rising threats in cyberspace is the building of a more coherent global system of intelligence and defense. The idea of a global cyber defense alliance or coalition of nations working together against cyber threats is gaining popularity.
International Cybersecurity Alliances
With the rapidly changing landscape of cyber threats, single-handed national efforts are never sufficient to create an impregnable cyber realm for any nation to survive alone. As with so many challenges facing the nations of the world today, cyberattacks, these days, are highly sophisticated, with war crossing borders.
Therefore, international alliances would become invaluable for sharing threat intelligence, coordinating responses, and developing common Cybersecurity and Geopolitics strategies. Cyber alliances have started being fostered by such organizations as NATO and the European Union.
The cooperative cyber defense policy of NATO or EU efforts to advance common Cybersecurity and Geopolitics measures among member states may just be the start of these alliances. The more formalized and broad-based they become in the future will only ensure a much safer and resilient global infrastructure.
AI-Driven Shared Defense Systems
Two other dimensions that might start defining a paradigm shift are advanced cyber defense systems sharing among the nations and this AI and ML. These systems are designed to identify, analyze, and respond to threats in real time, giving nations the capability to detect and mitigate cyber risks before they blow out of proportion.
The AI-derived Cybersecurity and Geopolitics systems could also predict future threats through behavior analysis and pattern recognition across the digital landscape, ultimately giving nations a chance for more proactive defense against high-intensity attacks, be they cybercriminals, hackers, or even state-sponsored.”
Preparing Individuals and Organizations for the Resurgence of Threats:
In more complex world, harbinger threats have become proactive-action measures a person and organization before resolving any likely attack. Preparation concerns awareness, education, and strategy.
For Individuals: Cyber-Hygiene and Learning
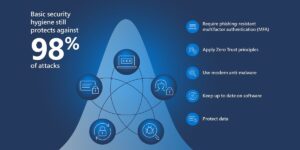
Individual citizens make up the first line of defence against all cyber threats. This is what is referred to today as cyber hygiene-habits such as updating your software regularly, using difficult, unique passwords, and being wary of phishing attacks.
Individuals need to know about the new and evolving cyber threats-articles detailing ransomware, deepfake technology, phishing scams, and other illicit online criminal activities. This knowledge will assist individuals in keeping abreast of developments in the latest tools and methods that cybercriminals employ and which they can use or avoid.
For Businesses: Protection Improvement and New Measures
Businesses should actively take a proactive approach to Cybersecurity and Geopolitics by carrying out routine risk assessments, robust employee training, and on top modern security such as firewalls, encryption, and multi-factor authentication, among others. In addition to securing their infrastructure, companies should not forget to craft a better-structured incident response plan in case of a cyberattack, ensuring quick and efficient recovery in the eventuality of a breach.
In addition to that, the future of Cybersecurity and Geopolitics for businesses would include collaboration with global networks of cybersecurity actors, through which threat intelligence-sharing practices and learning based on collective experiences are enabled. This effort in collaboration can help businesses remain a step ahead of cybercriminals and more effectively mitigate risks.
Government Role in Supporting Cybersecurity Readiness
In addition to this, governments must be active when it comes to making sure that individuals and businesses prepare themselves for the future of Cybersecurity and Geopolitics. Knowledge sharing by public-private partnerships builds national defense capabilities and completely institutionalizes knowledge in the future resilience of institutions in cybersecurity.
Governments may provide funding or incentives to businesses investing in Cybersecurity and Geopolitics measures and the creation of policies to persuade best practices for digital security. The increase of cyber threats mandates governments to formulate policies and frameworks along with the private sector for cybersecurity innovation, rapid threat detection, and improvement of response times.

Ahsan Ali is a technology blogger and the founder of Techzivo.com, a platform dedicated to delivering insightful and practical content for tech enthusiasts.He currently focuses on creating in-depth articles around cybersecurity, aiming to help readers stay safe and informed in the digital world. With a passion for emerging technologies, Ahsan plans to expand Techzivo’s coverage into other technology micro-niches such as AI, cloud computing, and digital privacy, offering valuable insights for a broader tech-savvy audience.