The second hand of the clock ticks against cybercriminal minds hammered to position-ever revisions of scams on vulnerable targets across all IT facades. But understanding the adversary is central to protecting oneself. By studying hackers’ minds, industries and IT managers can get hold of the secrets of infosec against all emerging threats. The guide is a treasure of information on hackers and will help you protect your systems irrespective of whether you are involved in cybersecurity Putting Yourself in the Mind of a Hacker, run a business, or are working in IT.
Understanding the Hacker Mindset
While hackers are usually associated with those dark basement figures, typing furiously away at code with line after line to create code, the reality is actually quite complex. The answer to understanding the putting yourself in the mind of a hacker cyber risk and why hackers do what they do is really knowing what motivates them to the act.
What Motivates Hackers?
Hackers have diverse motivations:
- Motivations for financial gain: It is the most common motivator for malicious actors: Cybercriminals will steal the confidential data either to sell it on the black market or to hold it for ransom.
- Political or ideologically motivated hacktivists: Political causes or injustice are often the cause of many hackers infiltrating systems.
- For thrill-seeking: There are those who hack systems for no other reason than to brag that they were able to do so.
- On the side of ethical hacking: These are the hackers who are not a threat. Ethical hackers or white hats help organizations identify vulnerabilities before these are exploited by malicious hackers.
Ethical vs. Malicious Hacking
In contrast to malicious hackers who put organizations under constant threat, ethical hackers become the guiding light for forming a basic structural defensive measure for cybersecurity Putting Yourself in the Mind of a Hacker. These White Hats put systems to the test by running simulation attacks. Knowing the difference is primary to formulating a response strategy.
Social Engineering: Exploiting Human Psychology
(Security weak links would definitely be worth a second consideration in cybersecurity.) In fact, the weakest link is sometimes not only the software but the human-to-software interface.
Human Element in Cybersecurity
Hackers depend on the old trick of human interference rather than system interference. Why? Because the humans are most likely to be trusting and errant and tend to overlook.
Some Common Tricks
Phishing
The attackers send emails pretending to be from trusted sources (for instance, a bank or a workplace) to trick users into clicking on malicious links or providing credentials.
Pretexting
Cybercriminals create a fabricated scenario designed to instill trust for the purpose of extracting confidential information, for example, by impersonating legitimate customer service personnel.
Baiting
Using enticing offers, such as “free movie downloads” or other tempting files, in some way tricks victims into downloading malicious files or clicking and executing harmful links.
These tactics, which incite fear, urgency, or even curiosity in the human mind, work.
Hacker Techniques: How They Bypass Security
Hackers utilize advanced techniques to exploit even the most robust systems. Here’s how they get past Cybersecurity Incident:
Penetration Testing and Red Team Operations
Some hackers apply penetration testing, much like ethical hackers, to probe organizational vulnerabilities. If gaps exist, malicious actors seize the opportunity.
Vulnerability Assessments and Exploit Methods
Hackers exploit vulnerabilities in outdated software, weak encryption, and unpatched systems to gain entry. For example:
- Outdated CMS platforms like WordPress often become hacking gateways.
- Advanced exploit kits target specific putting yourself in the mind of a hacker holes.
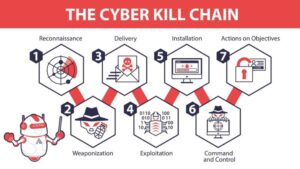
The Cyber Kill Chain: Steps of a Cyber Attack
A cyber attack is not an event but an unfolding process with phases. This series of events is called the cyber kill chain.
From Reconnaissance to Data Theft
Reconnaissance
Hackers collect information on their targets using open sources, corporate websites, or social media.
Weaponization
Crafting spear-phishing emails with malware or using malicious links intended for a specific victim.
Delivery
Delivery is when malware or phishing emails that are aimed at the target organization’s vulnerabilities are sent.
Exploitation
Malware exploits loopholes for privilege escalation.
Data Exfiltration
Sensitive files, emails, or financial records are stolen by hackers, which lead to devastating breaches in the system.
Case Studies in Real Life
SolarWinds Attack (2020)
The breach of SolarWinds gave an attack vector to hackers for some of the most significant companies and government agencies in the US, proving how even trusted supply chains can be weaponized.
Notorious Hacks and Lessons Learned
History is full of lessons from various famous hacks. Here are two well-known instances:
Kevin Mitnick
Known as the first infamous hacker, Mitnick, through social engineering, bypassed telecommunications systems in the late 80s. His apprehension made putting yourself in the mind of a hacker awareness a global issue.
Recent High-Profile Breache
Data breach of Equifax (2017)
unpatched vulnerabilities brought personal information of over 147 million Americans into the public domain. Take away: Updates are regular.
Colonial Pipeline Attack (2021)
A ransomware attack that shutdown fuel supplies and ransom payouts of millions in cryptocurrency. Suggests the need for stronger incident response protocols.
How to Defend Against Cyber Threats
“A chain is usually as strong as its weakest link; it is even more robust when there is no weak link. ” Threat mitigation starts with:
Security Awareness Training
Employees are your first line of defense. Continuous education and simulated phishing campaigns can reduce susceptibility to attacks.
Best Practices for Password Security
- Use strong, unique passwords for every service.
- Implement password managers.
- Enforce multi-factor authentication (MFA).
By minimizing human error, organizations can reduce attack vectors.
Incident Response: What to Do After a Breach
No system is foolproof. Once a breach is detected, here’s how to act:
Detection and Analysis
Determine what kind of breed of the mole, when and where he would have struck.
Containment
Isolate affected systems to prevent further infiltration.
Mitigation
Deploy patches and countermeasures to neutralize threats.
Digital Forensics
Trace attackers, identify how the breach occurred, and learn how to avoid similar future incidents.
Future Cyber Threats: AI and Advanced Attacks
At present, hackers are using the most sophisticated technology such as AI:
Threaths from AI
- Automated Bots: These mimic humans to bypass a CAPTCHA.
- Real-time Adaptive Malware: AI malware that adapts itself in real time to evade the detection.
Blockchain & Quantum Security
Blockchain adds a lot of transparency and decentralization, but in itself, it can be subjected to different kinds of attacks. For instance, with quantum computing, the risks doubled: regarding the vulnerabilities that quantum computing poses on current encryption models.
Staying ahead
In the fight against the threats, it needs to get blended-in with modern techniques of incorporating AI capabilities into cybersecurity Putting Yourself in the Mind of a Hacker tools and proactively rather than reactively.
Building a Strong Cyber Defense Strategy
Long-term protection isn’t about eliminating risk but minimizing exposure.
Regular Security Audits
Schedule vulnerability assessments to uncover and fix weaknesses proactively.
Zero-Trust Security Model
Adopt the “never trust, always verify” approach to ensure restricted access.
Invest in Threat Intelligence
In respect to putting yourself in the mind of a hacker updates and research, keep up with the dynamic threats over time, conferences like Black Hat or DEF CON. Updates should be kept on the latest developments of threats coming into perspective.
Continuous Vigilance is Key to Staying Ahead of Hackers
Because cybersecurity Putting Yourself in the Mind of a Hacker is an ongoing battle between two minds. The understanding of hackers on how they think and operate would definitely be the key toward protecting one organization. In-house training of employees with up-to-date putting yourself in the mind of a hacker practices would help in combating the commitment and flexibility necessitated.
Now it is time to put this knowledge to action. As you rethink your cybersecurity Putting Yourself in the Mind of a Hacker strategies, do not forget to continue learning and evolving along with the technology safe from hackers. Empower your people with hacker-proof strategies, come and talk to us.

Ahsan Ali is a technology blogger and the founder of Techzivo.com, a platform dedicated to delivering insightful and practical content for tech enthusiasts.He currently focuses on creating in-depth articles around cybersecurity, aiming to help readers stay safe and informed in the digital world. With a passion for emerging technologies, Ahsan plans to expand Techzivo’s coverage into other technology micro-niches such as AI, cloud computing, and digital privacy, offering valuable insights for a broader tech-savvy audience.