Your office may be bricks and mortar, but in the modern world, it is digital as well. And your digital infrastructure may often be even more precious than the physical one. Think about going to your building, all of your documents are gone, the lights are off, and the employees are locked out. That is what your business can do with a cyberattack.
How, then, do you prevent that?
The answer is simple—but layered: network security solutions.
This guide will reveal 18 tools that you must use to defend your virtual world against any breakout. We will demystify jargon and make it easier to understand while we demystify jargon and make it easier to understand, and this is how you will have a safer, smarter network if you are a small business owner or an IT enthusiast.
What Are Network Security Solutions?
How about network security solutions so that they work as a security device for your house in a digital way? You have the doors at home, put cameras, and even hire a dog as a guard, so you must have the same chances at home on the network.
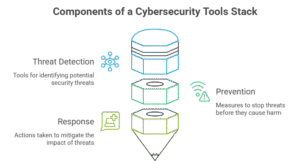
Such tools protect your data, prevent hacking, and keep your operations running smoothly. They prevent unauthorized access, identify threats in advance, and assist you in remediating threats before they turn uncontrollable.
Understanding Cyber Threats and Their Impact
Here’s a short story.
It seems that in 2022, a small e-commerce company believed it was too low-key to have been hacked. At one moment, all their customer data was encrypted with ransomware. They were not able to place the orders, they lost trust, and finally closed off.
It is not unusual. Cyber threats cut across the board, and they can strike at both individual and global businesses.
Therefore, when you believe you are too small to worry, think again.
Types of Network Security Solutions You Need
So, in simple words, what are the tools and examples that we can point out in real life?
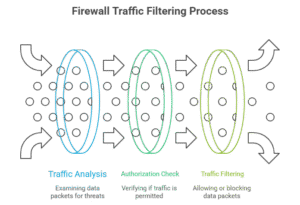
Firewall Protection
The firewall acts as a guard for your network. It isolates traffic- it picks and chooses what can join in or get out of your network, according to your designed rules.
There are different types:
- Traditional firewalls pass checks on addresses and ports.
- Next-generation firewalls (NGFWs) go further: they even examine their data, detect applications, and block malicious information.
- Web Application Firewalls (WAFs) protect a website against cross-site scripting attacks or SQL injection.
Anti-Malware and Endpoint Protection
Did you ever hear of viruses, worms, or ransomware? They are all malware.
Anti-malware software is your immune system. It searches files, prevents harmful downloads, and ensures that malware spreaders are kept away.
And the endpoint protection: the phones, tablets, and laptops should not sit unprotected.
Secure Remote Access with VPN
When you use a VPN, your information is wrapped in a safe channel, which comes to your rescue when you need to work outside or interface with a public Wi-Fi network.
It secures your channel, disguising your presence and any internet activity from hackers.
Zero Trust Architecture (ZTA)
This model has an approach that no one should be trusted automatically, not even those within an organization.
The Zero Trust Network Access (ZTNA) tools authenticate every user, device, and request and eventually give access.
Network Segmentation and Microsegmentation
Network segmentation divides your network into zones. If a hacker gets into one, they can’t access everything.
Microsegmentation takes it a step further, isolating workloads and sensitive data.
Security Monitoring Tools and Analytics
These tools offer real-time visibility into your digital environment.
- Security Analytics
- Network Monitoring
- Network Traffic Analysis
They help detect anomalies early.
Behavioral Analytics for Threat Detection
Behavioral analytics uses machine learning to understand normal patterns and flags anything odd. It’s essential for spotting insider threats.
Multifactor Authentication (MFA) and IAM
MFA is another layer of login security.
The ability to manage what is accessed by whom is called Identity and Access Management.
Compliance and Regulatory Requirements
The data protection standards ought to be adhered to in most industries. Such tools as SIEM and DLP will help to make compliance possible.
Cloud-Based Security and SASE
Businesses today are moving to the cloud. Secure Access Service Edge (SASE) is a networking and security solution incorporated into a unified cloud.
Security Orchestration and Automation (SOAR)
SOAR links various applications and automates the speed of responses to threats to be faster.
Managed & Extended Detection and Response (MDR & XDR)
MDR can provide monitoring at the expert level, whereas XDR introduces the high-end threat correlation across platforms.
Vulnerability Management and Patch Tools
Be ahead of the hackers by patching the holes before they do.
To eliminate those holes, resort to vulnerability scanners and patch management tools.
Step-by-Step: Building Your Security Stack
Step 1: Know Your Risks
- What data will you require to guard?
- Where is it held?
- Who is it available to?
Step 2: Choose Core Tools First
To begin with, use anti-malware, encryption, and firewalls.
Step 3: Add Layers
Install VPNs, SIEM, DLP, and email protection.
Step 4: Go Proactive
Employ ZTNA, analytics, and microsegmentation.
Step 5: Automate & Outsource
Install SOAR, MDR, and contemplate a SASE model.
Why Investing in Network Security Solutions Pays Off
Security does not mean protection only, as it is about continuity, trust, and growth.
Consider losing the data about your customers. Now, consider that you can prevent that attack in its inception. This is the strength of the right tools.
By going with network security solutions that offer you all the solutions you need, what you purchase is not only software, but you’re investing in peace of mind.
Final Thoughts
The world of the cyber is ever-changing, as well as the security barriers. These 18 network security tools are complementary, and one can create a fortress for your data.
If you own a mom-and-pop shop or a large multinational corporation, it is time to get your digital house in order.
Waiting until the breach does not help. Begin protecting your company now.
FAQs
1. What are the network security solutions?
Network security solutions refer to tools and technologies intended to keep the digital infrastructure safe against cyber threats. They are firewalls, antiviruses, intrusion detection, zero trust architecture, VPNs, endpoint protection, and SIEM. The combination allows them to keep track of unauthorized access, and detect and prevent data leaks in businesses.
2. What are the five types of network security?
The five types of network security that are commonly known include:
- Firewall protection– filters the traffic in and out
- Antivirus and anti-malware – find and eliminate malicious software
- Intrusion Detection and Prevention System (IDPS) – observes and prevents attacks
- Access control systems allow users to access the network only when authorized to do so
- Data loss prevention (DLP) -exports data leakage of sensitive information
A combination of these factors will form a good security position to keep pace with evolving cyber threats.
3. What are the different types of security solutions?
There are a number of types of security solutions:
- Network security products (e.g., firewalls, VPNs)
- Endpoint protection products (e.g., antivirus, EDR)
- Security cloud solutions (e.g., CASB, SASE)
- Protection of application (e.g., WAFs)
- (e.g., encryption, DEF, DLP) Data security
- (IAM) Identity and access management
All of them are significant to secure different scales of the IT infrastructure of an organization.
4. What are the top 5 solutions for cybersecurity?
The five best solutions suggested for excellent cybersecurity in contemporary enterprises are:
- Next-Generation Firewall (NGFW)
- EDR (Endpoint Detection and Response)
- Security Information and Event Management (SIEM)
- Zero Trust Network Access (ZTNA)
- Multifactor Authentication (MFA)
The tools assist in identifying, curbing, and reacting to cyber threats in real time.
5. What are the three main areas of network security?
The three most important domains of network security are:
- Physical security, Hardware, and infrastructure are shielded against physical interference
- Technical security– Comprises encryption, firewalls, and access control
- Administrative security– this entails security policies, employee training, and audits
An effective network security plan encompasses all three in order to avoid both external and internal attacks.

Ahsan Ali is a technology blogger and the founder of Techzivo.com, a platform dedicated to delivering insightful and practical content for tech enthusiasts.He currently focuses on creating in-depth articles around cybersecurity, aiming to help readers stay safe and informed in the digital world. With a passion for emerging technologies, Ahsan plans to expand Techzivo’s coverage into other technology micro-niches such as AI, cloud computing, and digital privacy, offering valuable insights for a broader tech-savvy audience.